
Last year, 28% of businesses saw an increase in physical security incidents, and 27% said they expected those to continue. However, even knowing the risks, 57% said they had not changed their security strategy. Among those who were increasing security, many were using tools like remote monitoring systems which don’t catch incidents until they happen.
For companies that are serious about making security a priority, policy-based access control (PBAC) is increasingly becoming the gold standard for managing access to a company’s systems. PBAC uses state-of-the-art credentialing and authorization technologies to automate access based on a zero-trust model in which everyone is assumed to be a potential bad actor until they can provide proof that they have the correct permissions.
Below, we’ll look at how PBAC features keep companies safe and lead the way in physical security measures.
Policy-based access control (PBAC) is a way of granting specific types of access to company assets based on a set of rules. These rules can take into account a person’s location, job role, rank, and much more. For example, if a person has management credentials, they may be granted access to certain systems and can perform specific actions that others cannot.
However, a lot more goes into setting up a sophisticated PBAC. It also requires creating multiple steps in a company’s system, such as Policy Enforcement and Decision Points (PEPs and PDPs), which check credentials and generate authorization requests based on very specific attributes and rules.
PBAC systems can use a combination of four types of attributes to determine if a user should be granted access to a system and what they can do once they’re in:
The combination of these attributes with policies is what makes PBAC unique. PBAC uses Boolean logic to parse whether an access request is legitimate and grants only the relevant access if all the conditions are correct. Systems are programmed to process the attributes in an “if, then” fashion – for example, a policy may state that if the person trying to gain access to a file while working from home is a manager and can show credentials (such as a password), then they can access a specific file folder. However, the formulas are typically more complex. For example, if a manager is trying to access a document on the company system, and if they are within a certain geographical area, then they may access and edit a file. But if it is between the hours of 12am and 5am, then they may only see and read the file.
As you can see, this could prevent someone with faulty credentials on the other side of the world from gaining undue access to a system (even if it locks out a manager working late). PBAC can provide more extensive control because it takes attributes and other rules into account but adds an extra layer that allows it to be dynamic.
Role-based access control (RBAC) is quite common in the workplace, but it’s simply not enough to deter savvy bad actors who want access to physical or digital assets. It’s also not flexible enough to offer access to those who need it based on more granular attributes, such as time, device, or location. For example, if all managers are given the same access, an inflexible RBAC policy may bar them from a new location or they may not be able to access company assets when they take on a new task without a title change.
The large categories used by RBACs require someone to constantly track an individual’s status in order to stay up to date. Neglecting to do so can cause both security risks and compliance issues, especially when permissions are not revoked when necessary.
Now that hybrid and remote work are so common, PBAC is more necessary than ever to prevent security incidents that can cause financial and reputational damage. With PBAC, access is provided on a need-to-know only basis, and can be tracked closely.
The pandemic brought sudden workplace closures, changing business hours, and staffing changes that still haven’t entirely returned to normal. This led to major security challenges as companies tried to keep up with how to control building and worksite access. Card-based security can be easily thwarted and typically offers 24/7 access to anyone who holds the card. But the problem can’t be solved by taking away employee access because companies also want workers to be maximally productive, meaning they must balance access with convenience.
PBAC attempts to solve the problem of tracking who gets access to a site or asset, when they have access, and what they can do once they’ve gained access. That access can also be amended in real-time in case of emergencies.
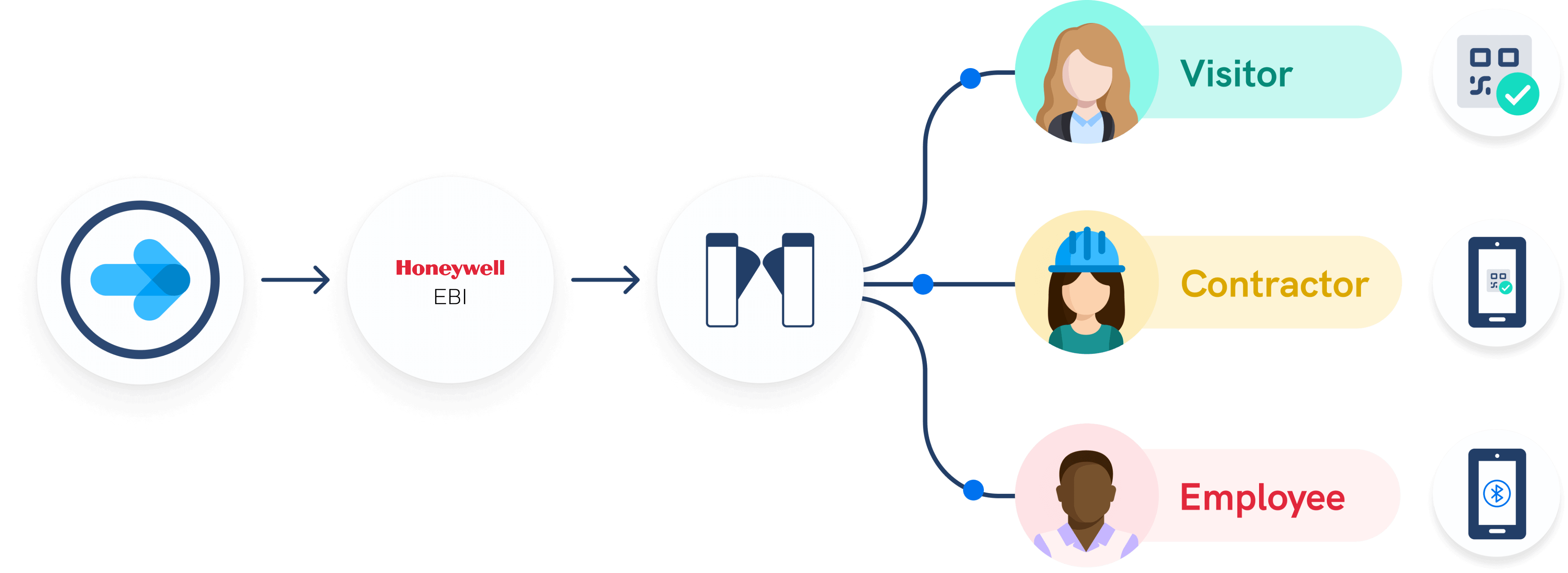
Most access control models use static rules to assign access and ignore the context in which the request is made. Overly broad categories can create security risks, while narrow ones keep employees from accessing the assets they need to do their work.
Access control solutions work in tandem with visitor management systems (VMS). A VMS such as Sine’s can scan in employees and visitors to check credentials, help employ geofencing to restrict access to certain parts of a work site, and be integrated into an access control system, such as the one offered by our partner, Gallagher. The use of QR codes, host notifications, and pre-registration are all points at which policies can be put in place to stop people from accessing sites where they shouldn’t be.
Interested in learning how to protect your business with Sine? Book a live demo with one of our product experts to find out how to get state-of-the-art physical security for your work sites.